Man In the Middle
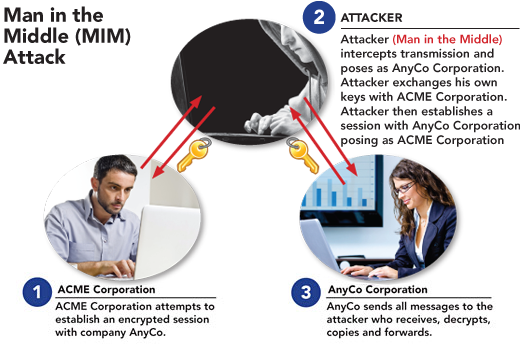
MItM (Man In the Middle) is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker.
Example: A hacker intercepts communication to a bank. The customers communicate with the hacker thinking the hacker is the bank. The hacker pretends to be the customer talking to the bank. Then the hacker collects user information and validated IP addresses.
The hacker steals from the bank by pretending to be legitimate users, often distracting IT staff with a detectable attack at the same time.
Defense: Banks look for irregularities with software using:
- Withdrawal patterns
- Money transfer patterns
- IP address used by customers
- Unusual amounts of activity for the day or time of day
The problem with all these approaches is they detect activity after the security has been breached.
Currently there is no way to detect MItM attacks in real time. Banks have to wait until the hacker is inside user accounts and the damage is done.
Examples:
